In today’s digital landscape, ensuring the security of your systems and applications is paramount. With the increasing sophistication of cyber threats, it’s crucial to have a robust understanding of how to test for security vulnerabilities. This guide provides a comprehensive overview of the techniques and best practices involved in identifying and mitigating potential security risks, empowering you to protect your assets effectively.
From penetration testing to vulnerability assessment and risk management, we’ll delve into the essential aspects of security testing. We’ll explore the tools and techniques used by security professionals, discuss industry standards and regulations, and highlight emerging trends shaping the future of this critical field.
Security Testing Overview

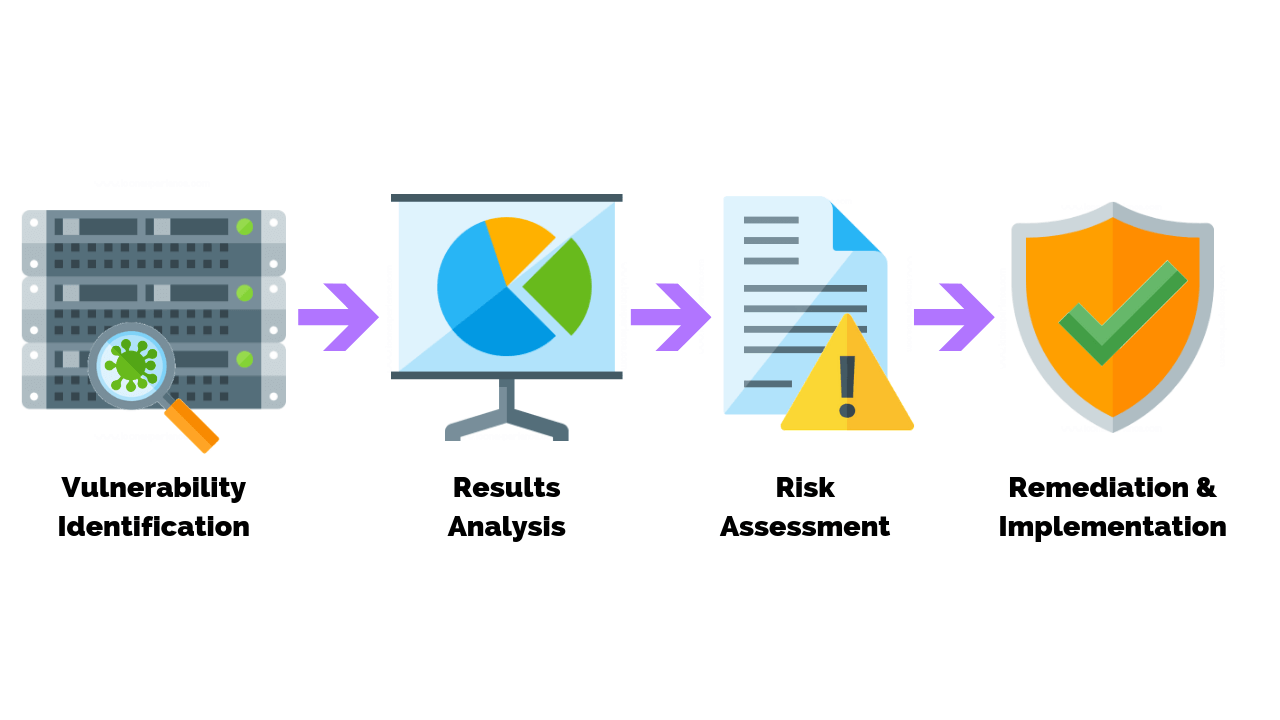
Security testing is the process of evaluating the security of a computer system, network, or application. It is important to perform security testing regularly to identify and fix vulnerabilities that could be exploited by attackers.
There are many different types of security testing, including:
- Penetration testing: Simulates an attack on a system to identify vulnerabilities.
- Vulnerability assessment: Scans a system for known vulnerabilities.
- Risk assessment: Identifies and evaluates the risks associated with a system.
Each type of security testing has its own benefits and limitations. Penetration testing is the most comprehensive type of security testing, but it can also be the most expensive and time-consuming. Vulnerability assessment is less comprehensive than penetration testing, but it is also less expensive and time-consuming. Risk assessment is the least comprehensive type of security testing, but it is also the least expensive and time-consuming.
Security Testing Tools
There are many different security testing tools available, including:
- Nessus: A vulnerability scanner that can identify thousands of vulnerabilities.
- Metasploit: A penetration testing framework that can be used to exploit vulnerabilities.
- Burp Suite: A web application security scanner that can identify vulnerabilities in web applications.
– Vulnerability Assessment Techniques
Vulnerability assessment techniques are systematic approaches used to identify, quantify, and prioritize vulnerabilities in a system or network. These techniques provide valuable insights into the security posture of an organization, enabling proactive measures to mitigate potential threats.
Vulnerability assessment techniques can be categorized based on their methodologies:
Network-based Techniques
- Port scanning: Scans network ports to identify open and listening services, which can reveal potential entry points for attackers.
- Network traffic analysis: Monitors network traffic to detect suspicious patterns or anomalies that may indicate malicious activity.
- Vulnerability scanning: Utilizes automated tools to scan for known vulnerabilities in network devices and systems.
Host-based Techniques
- System auditing: Reviews system logs, configuration files, and installed software to identify potential vulnerabilities or misconfigurations.
- Vulnerability scanning: Similar to network scanning, but specifically targets individual hosts within a network.
- Code review: Manual or automated analysis of source code to identify security flaws or vulnerabilities.
Manual Techniques
- Penetration testing: Simulates real-world attacks to identify vulnerabilities and assess the effectiveness of security controls.
- Security audits: Comprehensive reviews of an organization’s security posture, including vulnerability assessments, risk assessments, and compliance checks.
Automated Techniques
- Vulnerability scanning tools: Automated tools that scan for known vulnerabilities in a system or network.
- Intrusion detection systems (IDS): Monitor network traffic and system activity to detect and alert on potential attacks.
- Security information and event management (SIEM) systems: Collect and analyze security-related data from multiple sources to provide a comprehensive view of security events.
Selecting the appropriate vulnerability assessment technique depends on the specific requirements and constraints of the organization. Factors to consider include the scope of the assessment, available resources, and the level of expertise required.
Network Scanning
Network scanning involves systematically probing a network to identify and assess the security posture of connected devices. It helps uncover vulnerabilities, misconfigurations, and potential threats that could be exploited by malicious actors.
Network scanners are tools that automate the scanning process. They employ various techniques to gather information about network devices, including IP addresses, operating systems, services running, and open ports.
Types of Network Scanners
- Active Scanners: Actively probe devices by sending packets and analyzing responses. Examples include Nmap and Nessus.
- Passive Scanners: Monitor network traffic and gather information without actively interacting with devices. Examples include Wireshark and tcpdump.
- Hybrid Scanners: Combine active and passive scanning techniques to provide a more comprehensive view of the network.
Ethical Considerations
Network scanning can be considered intrusive, as it involves probing devices without their explicit consent. It’s crucial to obtain authorization before performing scans, especially on networks outside your control.
Interpreting Scan Results
Network scan results provide a wealth of information, including:
- Device IP addresses and hostnames
- Operating systems and versions
- Services running and their versions
- Open ports and their associated services
Network Vulnerabilities
Network scans can detect various vulnerabilities, such as:
- Open ports that expose sensitive services
- Outdated software with known security flaws
- Misconfigured devices that allow unauthorized access
- Weak or default passwords
Mitigation
To mitigate risks associated with network vulnerabilities, consider:
- Patching software and firmware regularly
- Configuring devices securely, including strong passwords and firewalls
- Restricting access to sensitive services and ports
- Implementing intrusion detection and prevention systems
Best Practices
Follow these best practices for network scanning:
- Obtain authorization before scanning
- Use reputable scanning tools and techniques
- Interpret results carefully and correlate with other sources
- Address vulnerabilities promptly and effectively
- Review and update scanning policies regularly
Penetration Testing
Penetration testing, also known as pen testing, is a cybersecurity technique that simulates an attack on a computer system, network, or application to identify security vulnerabilities that an attacker could exploit.
Penetration tests are typically conducted by ethical hackers, who are authorized to attempt to break into a system and identify any weaknesses. The goal of a pen test is to provide organizations with a detailed report of the vulnerabilities found, along with recommendations for how to fix them.
Phases of a Penetration Test
A penetration test typically involves the following phases:
- Reconnaissance: The tester gathers information about the target system, including its network architecture, operating system, and applications.
- Scanning: The tester uses automated tools to scan the target system for vulnerabilities.
- Exploitation: The tester attempts to exploit the vulnerabilities identified in the scanning phase.
- Reporting: The tester provides a report to the organization detailing the vulnerabilities found and the recommendations for fixing them.
Penetration Testing Tools
There are a number of different penetration testing tools available, including:
- Nmap: A network scanner that can identify open ports and services on a target system.
- Metasploit: A framework for developing and executing exploits.
- Burp Suite: A web application security scanner.
- Nessus: A commercial vulnerability scanner.
Web Application Security Testing

Web application security testing is a specialized branch of security testing that focuses on identifying and exploiting vulnerabilities in web applications. These vulnerabilities can allow attackers to gain unauthorized access to sensitive data, compromise the integrity of the application, or disrupt its availability.
Web application security testing is unique in that it requires a deep understanding of both web application development and security principles. Testers must be able to identify potential vulnerabilities in the application’s code, configuration, and deployment environment. They must also be able to exploit these vulnerabilities to demonstrate the impact they could have on the application.
Types of Web Application Security Testing Tools
There are a variety of web application security testing tools available, each with its own strengths and weaknesses. Some of the most popular tools include:
- Automated scanners: These tools use automated techniques to scan web applications for vulnerabilities. They can be used to identify a wide range of vulnerabilities, but they can also be time-consuming and resource-intensive.
- Manual testing: This involves manually testing the application for vulnerabilities. It is more time-consuming than automated testing, but it can be more effective at identifying complex vulnerabilities.
- Penetration testing: This involves simulating an attack on the application to identify vulnerabilities. It is the most comprehensive type of web application security testing, but it is also the most expensive and time-consuming.
Examples of Web Application Security Testing Techniques
There are a variety of web application security testing techniques that can be used to identify vulnerabilities. Some of the most common techniques include:
- Input validation testing: This involves testing the application’s input validation mechanisms to ensure that they are properly handling user input.
- Authentication and authorization testing: This involves testing the application’s authentication and authorization mechanisms to ensure that they are properly protecting access to sensitive data.
- Session management testing: This involves testing the application’s session management mechanisms to ensure that they are properly protecting user sessions from unauthorized access.
- Data encryption testing: This involves testing the application’s data encryption mechanisms to ensure that they are properly protecting sensitive data from unauthorized access.
Mobile Application Security Testing
Mobile application security testing is the process of evaluating the security of mobile applications to identify and address vulnerabilities that could compromise user data, privacy, or device functionality. Specific considerations for mobile application security testing include:
– The diverse range of mobile platforms and devices, each with its own unique security features and vulnerabilities.
– The use of mobile applications for sensitive tasks, such as banking, shopping, and accessing personal information.
– The potential for mobile applications to be targeted by malicious actors seeking to exploit vulnerabilities for financial gain or other malicious purposes.
Cloud Security Testing
Cloud security testing is a critical aspect of ensuring the security of cloud-based systems and applications. The unique challenges of cloud security testing include:
- Shared responsibility model: In the cloud, the responsibility for security is shared between the cloud provider and the customer. This can make it difficult to determine who is responsible for testing and securing the system.
- Dynamic environment: Cloud environments are constantly changing, with new services and features being added all the time. This can make it difficult to keep up with the latest security threats and vulnerabilities.
- Multi-tenancy: Cloud environments are often shared by multiple customers, which can increase the risk of security breaches.
Types of Cloud Security Testing Tools
There are a variety of cloud security testing tools available, each with its own strengths and weaknesses. Some of the most common types of cloud security testing tools include:
- Vulnerability scanners: These tools scan cloud environments for known vulnerabilities. They can be used to identify potential security risks and weaknesses.
- Penetration testing tools: These tools simulate attacks on cloud environments to identify vulnerabilities that could be exploited by attackers.
- Web application security scanners: These tools scan web applications for vulnerabilities that could allow attackers to compromise the application.
- Cloud security posture management (CSPM) tools: These tools provide a centralized view of the security posture of a cloud environment. They can be used to monitor for security threats and vulnerabilities, and to track compliance with security regulations.
Cloud Security Testing Techniques
There are a variety of cloud security testing techniques that can be used to identify and mitigate security risks. Some of the most common cloud security testing techniques include:
- Network scanning: This technique involves scanning the cloud environment for open ports and vulnerabilities. It can be used to identify potential entry points for attackers.
- Penetration testing: This technique involves simulating attacks on the cloud environment to identify vulnerabilities that could be exploited by attackers.
- Web application security testing: This technique involves testing web applications for vulnerabilities that could allow attackers to compromise the application.
- Cloud security posture management (CSPM): This technique involves monitoring the security posture of a cloud environment and tracking compliance with security regulations.
Social Engineering Testing
Social engineering testing evaluates an organization’s susceptibility to social engineering attacks, which exploit human weaknesses to gain access to sensitive information or systems. These attacks aim to trick individuals into divulging confidential data or performing actions that compromise security.
Types of Social Engineering Attacks
Social engineering attacks come in various forms, including:
- Phishing: Sending fraudulent emails or messages that appear legitimate to trick recipients into revealing personal information or clicking on malicious links.
- Vishing: Making phone calls that mimic legitimate organizations to obtain sensitive information.
- Smishing: Sending text messages containing malicious links or requests for personal information.
- Tailgating: Physically following authorized individuals into restricted areas without proper credentials.
- Dumpster diving: Searching through discarded documents or trash to find sensitive information.
Social Engineering Testing Techniques
Social engineering testing involves simulating these attacks to assess an organization’s vulnerability and identify areas for improvement. Techniques include:
- Email phishing: Sending simulated phishing emails to employees to test their awareness and response.
- Phone vishing: Making phone calls to employees to evaluate their susceptibility to social engineering tactics.
- Physical penetration testing: Attempting to gain unauthorized access to facilities by posing as legitimate visitors or contractors.
- Social media reconnaissance: Gathering information about employees and the organization through social media platforms.
Reporting and Remediation: How To Test For Security Vulnerabilities
Reporting and remediation are critical steps in the security testing process. Proper reporting ensures that the results of the testing are communicated effectively to stakeholders, while remediation involves taking steps to address the vulnerabilities that have been identified.
Types of Security Testing Reports
There are different types of security testing reports, each with its own purpose and audience. Some common types include:
- Executive Summary: Provides a high-level overview of the testing results for senior management or other non-technical stakeholders.
- Technical Report: Provides detailed information about the testing methodology, findings, and recommendations for remediation.
- Remediation Plan: Artikels the specific steps that need to be taken to address the vulnerabilities that have been identified.
Remediating Security Vulnerabilities
Remediating security vulnerabilities involves taking steps to address the underlying causes of the vulnerabilities and prevent them from being exploited. This can involve a variety of measures, such as:
- Patching software: Applying software updates to fix known vulnerabilities.
- Configuring systems securely: Ensuring that systems are configured in a way that minimizes the risk of exploitation.
- Implementing security controls: Deploying firewalls, intrusion detection systems, and other security controls to protect systems from attack.
Benefits of Automated Reporting Tools
Automated reporting tools can provide a number of benefits, including:
- Consistency: Ensures that reports are generated in a consistent format, making it easier to compare results over time.
- Time savings: Reduces the amount of time required to generate reports, freeing up security analysts to focus on other tasks.
- Improved accuracy: Eliminates the risk of human error in the reporting process.
Writing Security Testing Reports
When writing security testing reports, it is important to:
- Be clear and concise: Use simple language that is easy to understand.
- Provide evidence: Support your findings with evidence, such as screenshots or logs.
- Prioritize vulnerabilities: Rank the vulnerabilities that you have identified based on their severity and risk.
- Recommend remediation steps: Provide specific recommendations for how to remediate the vulnerabilities that you have identified.
Remediation Techniques
Different remediation techniques can be used to address different types of vulnerabilities. Some common techniques include:
- Patching: Applying software updates to fix known vulnerabilities.
- Configuration hardening: Configuring systems in a way that minimizes the risk of exploitation.
- Security controls: Deploying firewalls, intrusion detection systems, and other security controls to protect systems from attack.
- Penetration testing: Simulating an attack on a system to identify vulnerabilities and weaknesses.
Table of Security Testing Reports
The following table summarizes the different types of security testing reports and their key characteristics:
| Report Type | Purpose | Audience | Key Characteristics |
|—|—|—|—|
| Executive Summary | Provides a high-level overview of the testing results | Senior management or other non-technical stakeholders | Concise, easy to understand, non-technical language |
| Technical Report | Provides detailed information about the testing methodology, findings, and recommendations for remediation | Security analysts, developers, and other technical staff | Detailed, technical language, includes evidence and analysis |
| Remediation Plan | Artikels the specific steps that need to be taken to address the vulnerabilities that have been identified | IT staff, security analysts, and other stakeholders responsible for implementing remediation | Specific, actionable steps, prioritized based on severity and risk |
Remediation Process Flowchart
The following flowchart Artikels the remediation process:
- Identify vulnerabilities: Conduct security testing to identify vulnerabilities in systems and applications.
- Prioritize vulnerabilities: Rank the vulnerabilities based on their severity and risk.
- Develop remediation plan: Artikel the specific steps that need to be taken to address the vulnerabilities.
- Implement remediation plan: Take the necessary steps to remediate the vulnerabilities.
- Verify remediation: Conduct follow-up testing to verify that the vulnerabilities have been successfully remediated.
Checklist for Remediating Security Vulnerabilities
The following checklist can be used to help remediate security vulnerabilities:
- Identify the root cause of the vulnerability.
- Determine the impact of the vulnerability.
- Prioritize the vulnerability based on its severity and risk.
- Develop a remediation plan.
- Implement the remediation plan.
- Verify that the vulnerability has been successfully remediated.
Common Security Testing Tools
The following is a list of common security testing tools and their features:
| Tool | Features |
|—|—|
| Nessus | Vulnerability scanner that identifies vulnerabilities in systems and applications |
| Burp Suite | Web application security testing tool that identifies vulnerabilities in web applications |
| Metasploit | Penetration testing tool that simulates attacks on systems and applications |
| Wireshark | Network protocol analyzer that can be used to identify network vulnerabilities |
Glossary of Terms, How to test for security vulnerabilities
The following is a glossary of terms related to reporting and remediation:
- Vulnerability: A weakness in a system or application that can be exploited by an attacker.
- Remediation: The process of taking steps to address a vulnerability and prevent it from being exploited.
- Security testing report: A document that summarizes the results of security testing and provides recommendations for remediation.
- Executive summary: A high-level overview of the testing results for senior management or other non-technical stakeholders.
- Technical report: A detailed report that provides information about the testing methodology, findings, and recommendations for remediation.
- Remediation plan: A document that Artikels the specific steps that need to be taken to address the vulnerabilities that have been identified.
Best Practices for Security Testing
Security testing is an essential part of any organization’s security strategy. By following best practices, organizations can ensure that their security testing is effective and efficient.
Some of the best practices for security testing include:
- Regular testing: Security testing should be performed regularly to ensure that systems are secure and up-to-date.
- Automation: Automation can help to improve the efficiency and effectiveness of security testing.
- Use of multiple testing techniques: Different security testing techniques can be used to identify different types of vulnerabilities.
- Involvement of stakeholders: Stakeholders should be involved in the security testing process to ensure that their needs are met.
- Communication of results: The results of security testing should be communicated to stakeholders in a clear and concise manner.
Importance of Regular Security Testing
Regular security testing is important for several reasons:
- It helps to identify vulnerabilities that could be exploited by attackers.
- It helps to ensure that systems are compliant with security regulations.
- It helps to improve the overall security posture of an organization.
Role of Automation in Security Testing
Automation can play a significant role in security testing by:
- Improving the efficiency of testing.
- Reducing the cost of testing.
- Increasing the accuracy of testing.
Industry Standards and Regulations
Security testing is governed by various industry standards and regulations that set forth requirements for organizations to ensure the security of their systems and data. Complying with these standards and regulations is essential for organizations to protect their assets, maintain customer trust, and avoid legal liabilities.
Key Industry Standards and Regulations
- ISO 27001: International standard for information security management systems (ISMS), providing a framework for organizations to establish, implement, maintain, and continually improve their ISMS.
- NIST Cybersecurity Framework (CSF): A voluntary framework developed by the National Institute of Standards and Technology (NIST) to help organizations identify, protect, detect, respond to, and recover from cybersecurity incidents.
- PCI DSS: Payment Card Industry Data Security Standard, a set of requirements for organizations that process, store, or transmit credit card data.
- HIPAA: Health Insurance Portability and Accountability Act, a US federal law that protects the privacy and security of health information.
- GDPR: General Data Protection Regulation, an EU regulation that protects the personal data of individuals within the European Union.
Benefits of Compliance
Complying with industry standards and regulations provides several benefits for organizations, including:
- Enhanced security posture
- Reduced risk of data breaches and cyberattacks
- Improved customer trust and confidence
- Legal compliance and avoidance of penalties
- Increased operational efficiency and cost savings
Compliance Guidance
To comply with industry standards and regulations, organizations should:
- Establish a clear security policy and framework.
- Conduct regular security assessments and testing.
- Implement appropriate security controls and technologies.
- Train and educate employees on security best practices.
- Monitor and review security logs and events regularly.
- Establish incident response plans and procedures.
Resources for Compliance
- NIST Cybersecurity Framework: https://www.nist.gov/cyberframework
- ISO 27001 Information Security Management System: https://www.iso.org/iso-27001-information-security.html
- PCI DSS Security Standards Council: https://www.pcisecuritystandards.org/
- HIPAA Technical Safeguards: https://www.hhs.gov/hipaa/for-professionals/security/technical-safeguards/index.html
- GDPR Information Portal: https://gdpr-info.eu/
Table of Key Requirements
| Standard/Regulation | Key Requirements |
|---|---|
| ISO 27001 | Establish an ISMS, conduct risk assessments, implement security controls, monitor and review security, incident response planning |
| NIST CSF | Identify security objectives, prioritize risk management, implement security controls, monitor and evaluate security, incident response planning |
| PCI DSS | Protect cardholder data, establish security controls, maintain a secure network, monitor and test security, incident response planning |
| HIPAA | Protect patient health information, implement security measures, conduct risk assessments, incident response planning |
| GDPR | Protect personal data, obtain consent, provide data subject rights, data breach notification, incident response planning |
Glossary of Terms, How to test for security vulnerabilities
- Information Security Management System (ISMS): A framework for managing and protecting an organization’s information assets.
- Security Control: A measure or mechanism used to protect an asset from threats.
- Incident Response Plan: A plan that Artikels the steps to be taken in the event of a security incident.
- Data Subject: An individual whose personal data is processed by an organization.
Flowchart for Compliance
- Establish a security policy and framework.
- Conduct a security assessment.
- Implement security controls and technologies.
- Train and educate employees.
- Monitor and review security logs and events.
- Establish an incident response plan.
- Review and update compliance status regularly.
Compliance Checklist
- Does your organization have a clear security policy and framework?
- Has your organization conducted a security assessment?
- Has your organization implemented appropriate security controls and technologies?
- Have your employees been trained and educated on security best practices?
- Does your organization monitor and review security logs and events regularly?
- Does your organization have an incident response plan in place?
- Does your organization review and update its compliance status regularly?
Sample Compliance Report
A compliance report is a document that demonstrates an organization’s compliance with a specific standard or regulation. It typically includes the following information:
- Description of the standard or regulation
- Organization’s compliance status
- Evidence of compliance
- Recommendations for improvement
Ethical Considerations in Security Testing
Conducting security testing requires adhering to ethical guidelines to protect the privacy and integrity of individuals and organizations. Ethical considerations involve obtaining informed consent, respecting data privacy, and avoiding malicious or destructive actions.
Obtaining Consent
Before conducting security testing, it is crucial to obtain informed consent from the organization or individuals whose systems will be tested. This consent should clearly Artikel the scope, objectives, and potential risks of the testing.
Respecting Data Privacy
Security testing should be conducted in a manner that respects data privacy and confidentiality. Testers must only access and collect data necessary for the testing purposes and ensure its proper disposal after the testing is complete.
Responsible and Ethical Conduct
Security testing should be conducted in a responsible and ethical manner, avoiding any actions that could compromise the integrity or availability of the target systems. Testers should use appropriate tools and techniques and adhere to industry best practices.
– Elaborate on the key drivers behind these emerging trends.
The rapid evolution of technology and the increasing sophistication of cyber threats are the primary drivers behind the emerging trends in security testing.
The growing adoption of cloud computing, mobile devices, and the Internet of Things (IoT) has expanded the attack surface and created new vulnerabilities that need to be addressed.
Additionally, the increasing use of artificial intelligence (AI) and machine learning (ML) in cyberattacks has made it more difficult for traditional security testing methods to detect and prevent these attacks.
Key Drivers
- Rapid evolution of technology
- Increasing sophistication of cyber threats
- Growing adoption of cloud computing, mobile devices, and IoT
- Increasing use of AI and ML in cyberattacks
Epilogue

By understanding how to test for security vulnerabilities, you gain the knowledge and skills to safeguard your systems, protect sensitive data, and maintain compliance with industry standards. Embrace a proactive approach to security testing, and stay ahead of potential threats to ensure the integrity and resilience of your digital assets.
Quick FAQs
What is the importance of security testing?
Security testing helps identify and address vulnerabilities in systems and applications, reducing the risk of cyber attacks and data breaches.
What are the different types of security testing?
Common types of security testing include penetration testing, vulnerability assessment, risk management, and social engineering testing.
What are the benefits of regular security testing?
Regular security testing helps ensure systems remain secure, identifies emerging threats, and demonstrates compliance with industry standards.
